IPC W2 Class1
That'll be fixed going forward.
Highlight
And then I'm gonna fly right into this week's topic
- jump right into
I'm getting a little behind here
getting practice on how to submit your work. Nonetheless, cover that
we're now in week2 (this is 13th to the 17th)
which should be available as of now, but(actually no time restrictions)
I think it's 8 o'clock it becomes available to you, you feel free to go ahead and play with that
Quiz Correction : 16minutes to do this quiz
only 1 attempt unlike last weeks, where you had 3 attempt
available for 24hours of the period, starting Friday at 18:00 (sixteen hundred hours EST)
------
1) workshop01.pdf
2) rubric.pdf
take a moment and look at the reflection rubric
only use matrix.senecacollege.ca
1. Intro. to Workshop #1 (Due this week)
Output : how to print sth(which is output)
- W2 : github - download ZIP and extract
- Part 1 : due by Thursday midnight
- Part 2 : due by Sunday at by midnight
- Worth : 1% of final grade
Outcomes
1) getting used to using VS , being able to create the simple C program
2) how you're remotely connecting to the Matrix server
- you're gonna be logging in a SSH(Secure Shell)
- you're gonna be transferring files using a SFTP(Secure File Transfer Protocol)
- you can submit your work to me
This includes your reflect.txt file you must submit for the part2
Part2 Reflection 50% this week
- 3-4 sentences, but it should be able to cover all 3 questions
- a reasonably link-given but concise: Don't give him too long
- describe what's happening here and what these things are
- not expecting the technical workshop, but briefly describe why it's called by that name
- What's the secure part? what does that mean exactly? and how these are related to what we're doing in the workshop
A lot of workshops work this way
Part1 : 10% | Part2 : 40% | Part2 Reflection : 50%
- always include 4: Full Name, Student Number, Email Address, Section Information Code(NAA)
If you miss the deadline, you don't get marks for it
Part1 놓쳐도 Part2, Reflection 할 수 있는데 better get in touch..? (10:00)
Part2 is usaully an extensional part1, want a continuation
(technically can do part2 without having done part1)
But in most cases, you don't have a choice but to do the 1st part
the name of the source file should be exact, case-sensitive, character-sensitive
source file and reflection file have to be copied in the same directory on Matrix when you submit
make use of microsoft words for spelling checking for those of you who're struggling with English
you're using college-level English
Matrix (SSH client)
Recommendation: create directories called s1 - ipc144
WinSCP
copy it
PuTTy
compile it manually so that you can work on Linux environment
Also, just to check if you don't have any errors by your own compile and run it before submission
~cameron.gray/submit 144w1/NAA_p1
--> profName.profLastname/submit 144 week1/ section code_part1(or part2)
2. Highlight : Computers, compiler

Check that after class
For the presentation part(prepared stuff), all the files will be uploaded here(blackboard), including any additional source code that he also may not have even covered in the class(just additional codes that you can play with)
Any code that he actively code will be posted on Teams
Computers
We can see how far away the user is to integrate with the actual hardware, their machine.
The user is interacting with the software layer, which is the application we'll be creating so that the user can use the computer which involves the hardware.
The software, however, is the part that many new programmers don't realize.
Software applications that we made are all controlled and managed by the operating system.
Our applications can directly access hardware sometimes.
But actually, it's not.
When a software application tries to connect directly with the hardware device, it's either asking permission from the OS, and or using a device driver which is another software, framework that it uses in order to communicate with the hardware. Software no matter what is pretty far removed from the real power of the computer itself.
The OS is pretty much its gatekeeper. It instills all the security measures.
It is the one that says to your applications "Yes, I can give you memory"
It is easiest clearing a variable in your application. It's not you demanding it and getting it.
It's about you asking the OS "can you plz give me some memory to do that?"
You aren't as powerful as you think as an application developer.
At the end of the day, it's all about the OS giving you permission to do the actions that you coded in your program.
You should analyze the components of our CPU because as a programmer when we need to do highly perform an application, it all boils down to trying to limit and number of computations that you need to do to get sth done.
You can't really successfully do that without factoring in the architecture of what a CPU is and how it works.
Two separate chips on a RAM
ALU (Arithmetic Logic Unit)
- does calculations for integral number(whole numbers = integer)
- faster
FPA (Floating Point Accelerator)
- any floating-point type of calculation goes to a dedicated chip called the FPA
- requires more power, more resources to calculate floating-point calculations, so anything that's a fractional number.
The request coming in, getting decoded going through the control unit, and then being dispersed
Based on this request(what kind of calculation is the CPU having to do right now), is it an integral one? or a floating-point one? The CU decides how diverse where things get done. And if it's a floating-type calculation, it will divert it to that chip so that that will be faster. If it's an integer type or whole number calculation, it will divert it to the ALU chip.
Be more efficient because that's set up to work for whole numbers only.
- Way back, this used to be just one chip, and there wasn't any distinction back in the past (inefficient)
Primary Storage (35:46)
- deals with memory that is bad and or on part of your motherboard of your main computer system itself.
It's usually integrated with the motherboard itself.
- sits very close to the CPU (proximity)
& chip architecture & circuit tree that connects to the motherboard and to your CPU→ fast
- but usually quite limited
- Comes in two forms
ROM (Read Only Memory)
- persistent, not volatile in the sense that when power goes off, and then start it again, the information in that ROM chip will remain(be retained). It doesn't need to be erased or updated.
- in the old days, could not be updated (it literally was read-only. not modifiable), but that's not true today.
- Unless you purposely overwrite what's on there, it is persistent. It will not be lost.
RAM (Random Access Memory)
- highly recommend you try to have a system with these much RAM as possible (32GB)
it makes changes when doing 3D graphics, gaming.
- Applications these days are memory-hog(a computer program that uses a lot of memory), so RAM helps a lot.
- volatile. If you lose your power, anything that is stored in the chip is gone. Get reset every time.
# should know the distinction between ROM and RAM, but most primary storage
Secondary Storage
- slower, a lot less than primary storage
- now this is all shifting because with the advantage of m2 RAM, which is kinda hybrid between a SSD and a RAM. They're now blowing, and speed and hardware architecture is changing, kinda making these almost indistinguishable.
- As far as HDD, SSD exist, we're still gonna have this degree of separation(Primary | Second)
Information & Data Storage
Bit
the smallest representation for data in a computer system
1 unit
Nibble
4 bits, half a byte
back in the 60s, kinda old system (when memory was not available)
Byte
8 individual bits represent 1 byte
Programming Languages
| High Level : 3rd, 4th, 5th-generation language | Low Level : Machine language, Assembly language |
| 3rd : Procedural, C, C++, Java we still have syntax that we need to abide by one letting c but, for the most part, human readable 4th : database [SQL], Prolog, Matlab 5th : we won't learn.. machine learning, artificial intelligence next step of Python(3rd) the skills still emerging |
Machine: being the closest binary as you can get [ 0 | 1 ] when you develop an interface between hardware and the OS, they need to be coded in this language. very quick and efficient working close to almost binary language precocial drivers for devices get created precocial to the 3rd generation language(C, C++, Java) Compilers are composed of low-level languages that make that possible |
C is the purest of the 3rd generation languages, the basis of which many other languages are developed.
footprint of syntax that you need to know to create a program. very fast(performant), small subset
c++ is performant but is OOP, has lots of libraries
Compiler
act of changing a source code file that we write in a text file(.c)
convert that into binary executable code that allows us to run it(the OS can run).
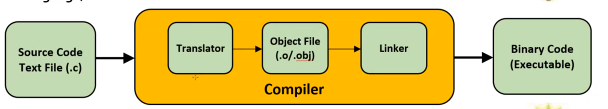
the highlight of what really goes on and all the little steps between
higher level of overview of what goes on
Translation: remaps all the syntax and puts it into the intermediate step of understanding so that the compiler knows how to translate your human words into the binary version of it.
Object File : the output of that translation will be compiled into an object file.
(more important when dealing with more than 1 file.)
it is technically a binary file, but not runnable(can't type the name it and expect to run)
Linker : if there're more than 1 obj file, it needs to combine into one executable binary file.
3. This week's Topics : Data Types, Simple Calculation, Expressions
Strongly suggest looking at the presentation file
summarize the important parts of your reading
56:00~